
Secure Your SaaS with Expert Testing
Break assumptions in auth, RBAC, IDOR & OAuth with our comprehensive testing services.
Trusted by SaaS founders
★★★★★
Penetration Testing Services
Comprehensive solutions for safeguarding your cloud environment and ensuring compliance.
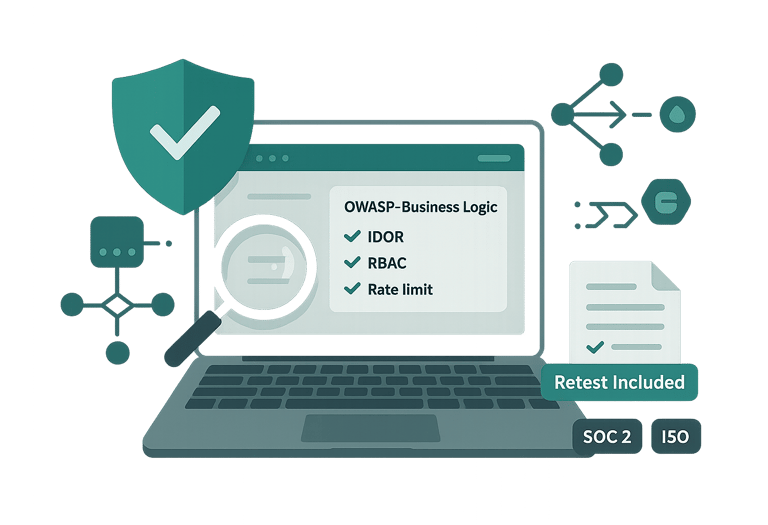
Essential Web App Pentest
Find and prove real-world risks in one web app-IDOR/RBAC, auth/session, rate-limits-then verify fixes with an included 30-day retest.
Web + API Pentest
Uncover and prove high-impact Web + API flaws—RBAC/IDOR/BOLA, OAuth/OIDC and rate-limit/race issues—with replayable Postman PoCs, prioritized fixes, and one retest within 45 days
Premium — SOC 2-Ready Security Assessment
Web + API pentest plus AWS posture review mapped to SOC 2/ISO—evidence pack, exec summary, attestation, and one retest within 60 days to unblock audits and deals.”

Scope: 1 web app
Focus: Manual testing of OWASP Top 10 + business-logic (IDOR/RBAC, auth/session, rate-limits)
Deliverables: Evidence-first PDF (risk matrix, PoCs, fixes), 60-min readout, attestation letter
Retest: One retest within 30 days (verify fixes)
Timeline: Typical 10–14 days end-to-end
Scope: Web app + REST/GraphQL APIs
Focus: Auth/OAuth-OIDC flows, RBAC/IDOR/BOLA, rate-limit & abuse paths, Postman PoCs
Deliverables: Everything in Essential + replayable Postman collection, prioritized remediation roadmap, evidence pack for questionnaires
Retest: One retest within 45 days
Timeline: 14 days typical (8–10 test days)
Scope: Web + API + light AWS posture review (CSPM-lite)
Focus: Business-logic abuse paths, attack-path analysis, control mapping to SOC 2 / ISO 27001
Deliverables: Executive summary for non-technical stakeholders, attestation + evidence pack, sign-off letter
Retest: One retest within 60 days
Timeline: 3 weeks (testing + reporting)
Common Questions
What is penetration testing?
Penetration testing simulates cyber attacks to identify vulnerabilities in your systems.
How long does testing take?
Testing duration varies by service, typically ranging from 10 - 60 days.
What is included in the service?
Our services include detailed reports, risk assessments, and retesting to ensure vulnerabilities are addressed.
Is my data safe?
Yes, we prioritise data security and confidentiality throughout the testing process.
How do I get started?
You can book a call or download a sample to begin.
Get in Touch
Reach out for a consultation or inquiries.


Connect
Get in touch for cybersecurity solutions.
CoNTACT
Subscribe
© 2025. All rights reserved.
